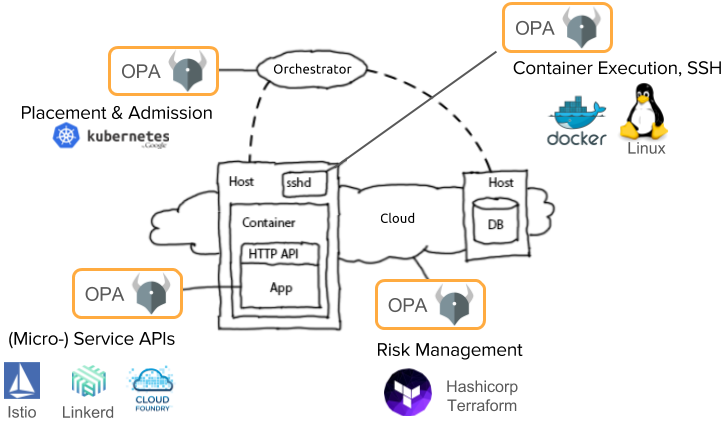
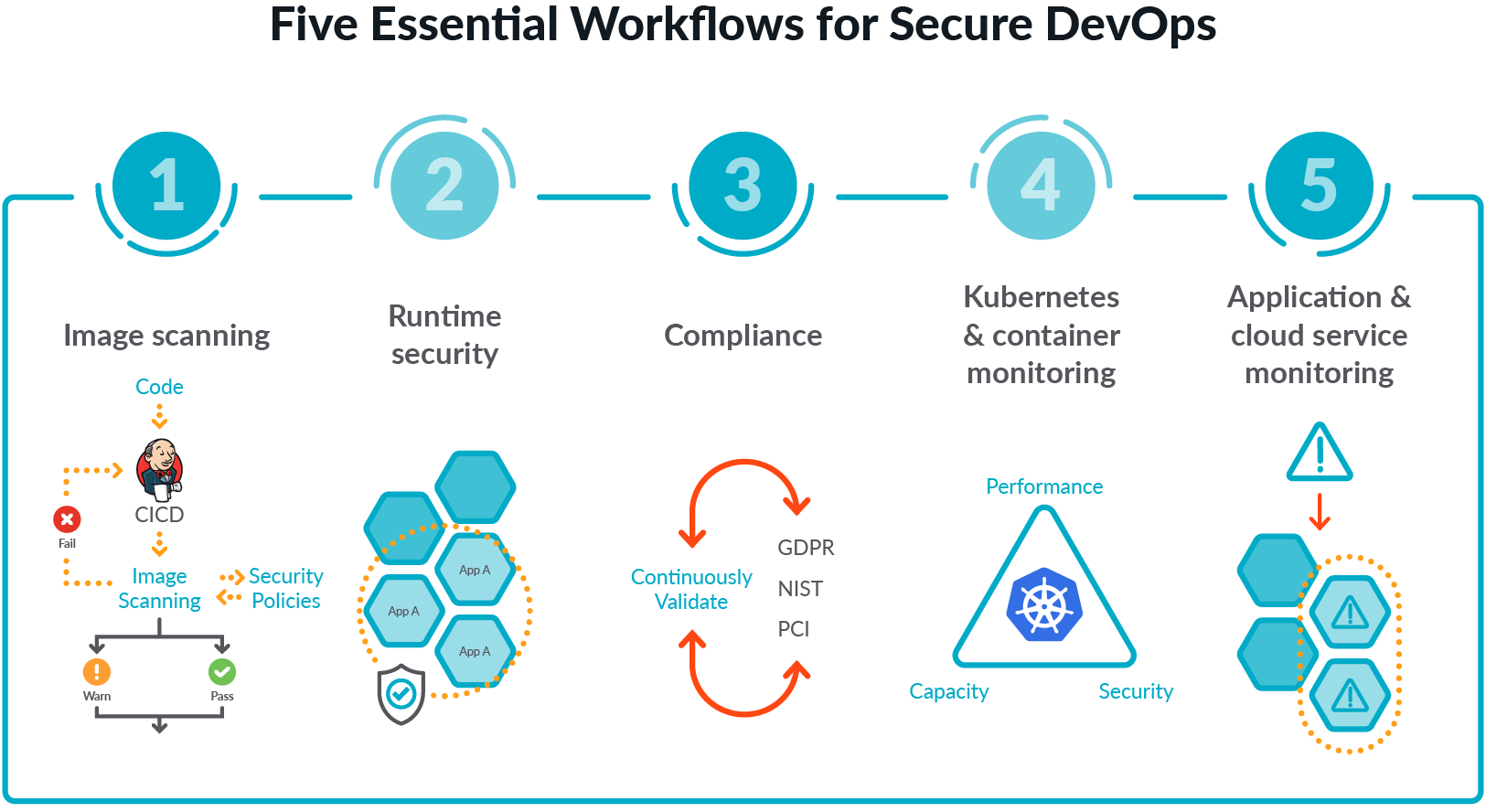
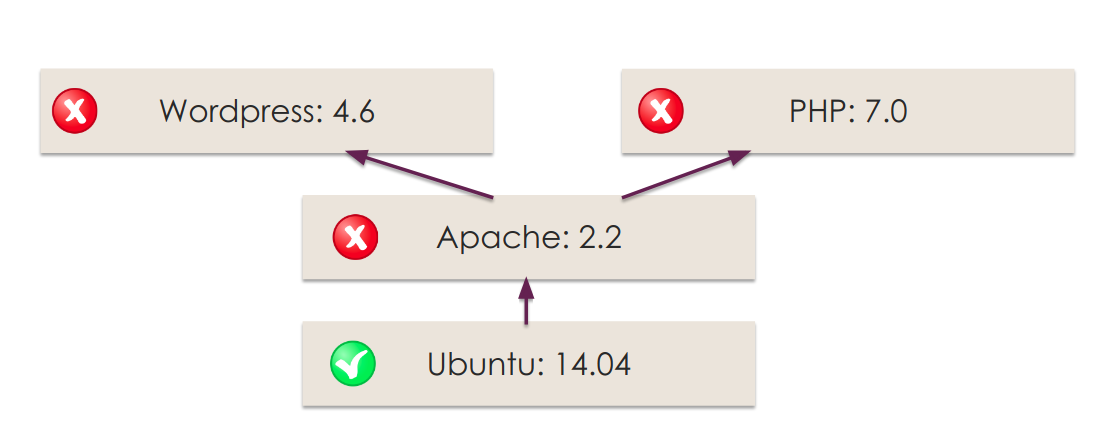
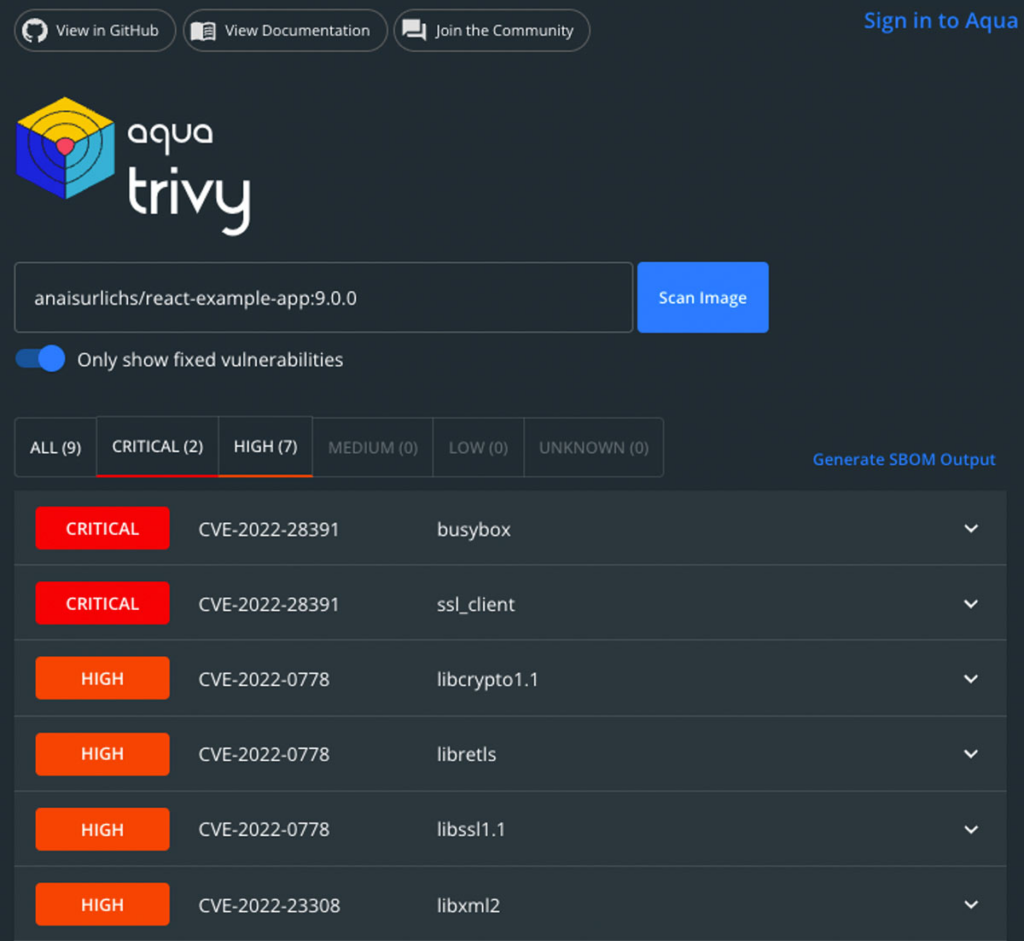
Docker Vulnerability Scanning Tools: Free, Open-Source, and Paid Options for Secure Container Images | by Hinanaseer | Medium

Scanning Docker Containers with Grype #docker #container #containersecurity #cloudsecurity - YouTube

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog